Our Managed Detection and Response (MDR) services are modular, so you can select one or several components. Once your Managed Threat Detection service is in place, it can be combined with a response service to complement your own abilities.
Define what's right for your business with expert advice
Try out our Managed Detection and Response Buyer’s Guide to find the best detection and response solution for your organization.
Incremental threat visibility and active response
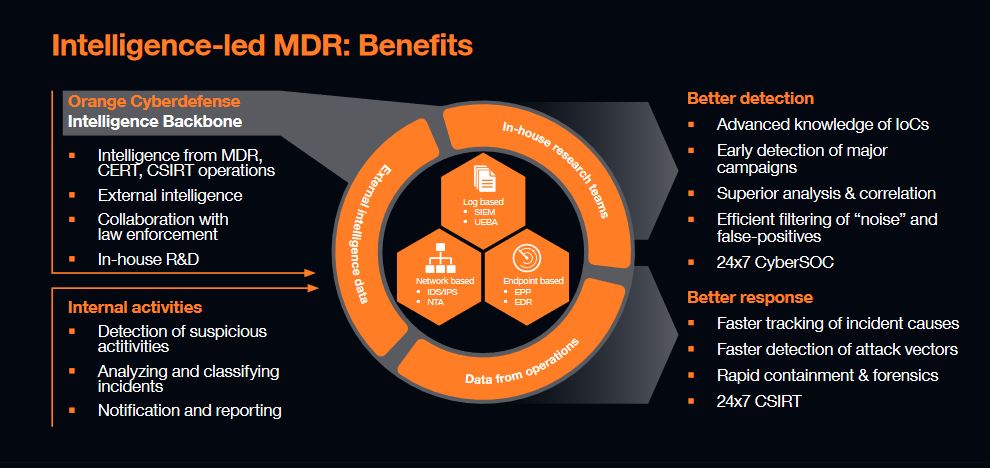
Threat Detection allows you to benefit from managed services or integrated complementary solutions based on SIEM, NTA (Network Traffic Analysis), EDR (Endpoint Detection and Response), XDR (Extended Detection and Response) and other technologies. All with the support of our expert consultants, SOC and CyberSOC analysts. We offer the following solutions:
Make the most of your security investment
Deployment based on where your business is today
Flexibility to adapt and evolve to future organizational needs via complementary modules
Include monitoring of cloud-based applications via APIs to cloud environments for consistent visibility of security events beyond the enterprise perimeter
Extend monitoring to operational technology security
Related products

