Among IT security goals, three topics are particularly important to users: data integrity (non-alteration of data), confidentiality (authorization for data access), and availability.
Here, in no particular order, is a set of 10 tools related to these themes that can help you safeguard data at your workstation. This list purposely excludes firewalls, anti-virus and anti-spyware software, as those applications deserve dedicated articles.
1. KeePass
Users are more and more plagued by the excess of passwords needed for email, Web interfaces, network readers and more. KeePass is one of the simplest and most user-friendly “password safe” solutions out there.
Passwords are encrypted when stored (Secure Hash Algorithm-256), and the entire database is in turn protected using the Advanced Encryption Standard (AES) algorithm. Also worth noting is the protection available of the KeePass process and the memory blocks used. A portable version is available for use with a USB flash drive in roaming mode.
KeePass is available at http://keepass.info/
2. TrueCrypt
It’s often useful to hide certain confidential corporate information from wandering eyes. TrueCrypt gives you the ability to quickly and easily create a “data safe” for storing your files.
In addition to creating an encrypted virtual reader that you link to a disk drive letter (eg Z:\), the application also lets you encrypt an entire partition, hard disk or removable disk. For the totally paranoid, it’s also possible to create a hidden data safe within an existing data safe (see the manual for more details on the benefits of this technique).
TrueCrypt is available at http://www.truecrypt.org/
3. AxCrypt
Similar to the approach taken by TrueCrypt, AxCrypt lets users carry out encryption/decryption operations unilaterally on a file (or a group of files).
Two functions make this application particularly user-friendly. First, users can generate an executable file that integrates decryption functions (when communicating an encrypted file to someone who doesn’t have AxCrypt, for example). Second, they can securely delete files using an algorithm for multi-cycle data replacement by random data pack.
AxCrypt is available at http://www.axantum.com/axcrypt/
4. Eraser
Looking for secure deletion solutions? You’ll find that the Eraser tool offers a more advanced approach than AxCrypt.
In addition to a wide variety of algorithms (Gutmann, US Department of Defense, Schneier, and other government specifications), file access can also be blocked during deletion. Also, content from other files can be added at the end of the process to "cover” your tracks. Another popular feature: scheduled “cleaning” operations at a set time on the same day every week or month.
Eraser is available at http://eraser.heidi.ie/
5. Microsoft Baseline Security Analyzer
Originally intended for small- and medium-sized businesses, MBSA has proved indispensable for users looking to determine the security level of their workstations in relation to Microsoft’s security recommendations.
On top of a security inventory, the application also provides lots of advice on specific corrective actions to take. It handles updates and configuration for the following Microsoft products: Windows 2000/XP/Vista/7, Windows Server 2003/2008/2008R2, Internet Information Services 5.0/5.1/6.0, Microsoft Internet Explorer 5.01/5.5/6.0, Microsoft SQL Server 7.0/2000/2005, and Office 2000/XP/2003.
MBSA is available at http://technet.microsoft.com/en-us/security/cc184923
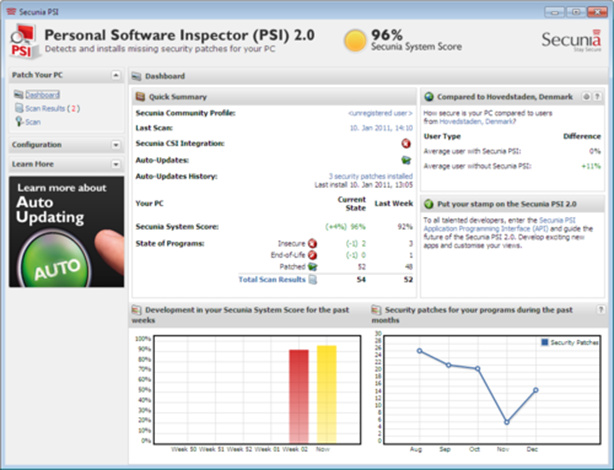
6. Personal Software Inspector
In the same spirit as MBSA, the company Secunia offers a more comprehensive tool that inspects much more than just the Microsoft ecosystem. For info, Secunia’s 2010 report stated that 50% of all vulnerabilities reported over the previous two years were found in products developed by the 14 major software companies.
A full analysis of executable files (exe, ocs, dll, etc) and Secunia signatures compile a report that shows users which versions are currently installed alongside a list of the latest versions available. The tool also offers the option of automatically patching applications.
Personal Software Inspector is available at http://secunia.com/vulnerability_scanning/personal/
7. Browser Check
Qualys, a company specializing in vulnerability audits, offers users an audit and consulting service for Web browsers. To use the tool, you have to install a browser add-on module, which is managed through the Qualys Browser Check portal.
In a Windows environment, the tool can detect non-updated versions of the following applications: security updates and operating system support, Adobe Flash / Shockwave Player, Adobe Reader, FoxIt Reader, Microsoft Silverlight, Java Engine, QuickTime multimedia players, Media Player and VLC (non-exhaustive list).
Browser Check is available at https://browsercheck.qualys.com/

8. FullSync
Users concerned about the availability of their data will certainly find this tool to be a step in the right direction. Simple and user-friendly, it’s an easy application to pick up.
The application supports local and network file systems accessible through FTP, SFTP, and SAMBA. With the ability to schedule synchronizations by minute, hour, day of the month, day of the week, or month, there’s nothing left for users to do but choose their duplication method: source replacement or synchronization.
FullSync is available at http://fullsync.sourceforge.net/
9. Backup Chunker
While in the same vein as the previous application, Backup Chunker is more user-friendly. However, the features offered in its freeware version are fairly comparable.
Backup Chunker is different than FullSync: it includes a more advanced configuration system (especially the inclusion/exclusion parameters) and Web Distributed Authoring and Versioning (WebDAV) protocol support. A professional version lets users set up more complex synchronization scenarios, such as simultaneous multi-device synchronization.
Backup Chunker is available at http://www.xarka.com/chunker/
10. Yours
Of course this list would not be complete without your tool of choice. Most likely, you’re making daily use of a tool that’s not listed here.
I invite you to post a comment and tell us about your tool, what its benefits / special features are, and what makes it original.

I work for Orange Business as a security leader within Products and Services Development. My previous jobs as a technical "worker bee" lead me to pay specific attention to the difficulties of implementing companies' security strategies and policies. Security, efficiency and pragmatism are my main pillars.