taginlineimportWhat happens when a smartphone without a security system is left in the middle of an urban jungle? Experts from Symantec have tried to answer this question with the "Smartphone Honey Stick" project.
the honey pot
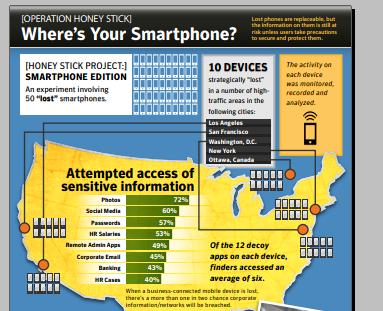
In cooperation with Perspective Inc., Symantec researchers had the (bad?) idea of “losing” 50 smartphones in the middle of five major North American cities: New York, Washington DC, Los Angeles, San Francisco and Ottawa. Abandoned in busy public spaces, the 50 smartphones contained applications that tracked their location and use.
Since smartphones hold valuable personal and professional information, the Symantec researchers were interested to see how people who stumbled across the devices would behave.
"lost" smaprtphones
The 50 smartphones had no security system (password, etc). As stated in "The Symantec Smartphone Honey Stick Project," the study aimed to analyze “human threats” to phones. It was designed to determine the probability that the finder of a device would:
- unlock the phone (and the time it would take to do so)
- access professional data and applications
- access personal data and applications
- access applications depending on type
- return the smartphone to its owner
- take the smartphone with him/her (and the time it would take to do so)
The researchers assumed that the finder would access the phone’s data or applications for one of the following reasons:
- identifying or locating the owner to return the device
- reading content for curiosity’s sake
- researching valuable information
- using it personally (calls, Internet access)
- resetting the phone for resale or reuse
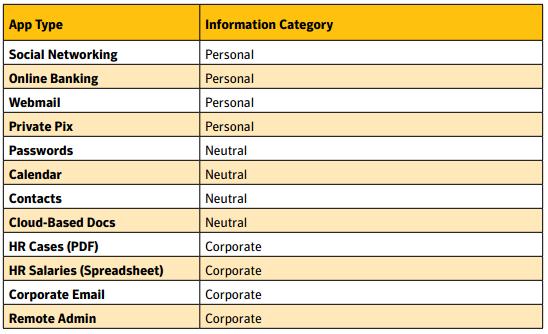
rigged applications and data
Every smartphone had a set of improperly functioning applications with easy-to-understand names and icons. In some cases, applications simulated a malfunction by sending an error message to the user:
Source Symantec Smartphone Honey Stick Project
The purpose of these applications was to collect data on user activity and communication. A GPS tracking device was also implemented to track the smartphone’s movements.
Certain applications asked the user to enter a password, but then authenticated the user with a pre-filled code. The list of contacts was short and included a “Me” entry, making it easy to identify the phone’s owner.
interesting results ?
When looking at the results of the Symantec study, we must keep in mind that the sample size was small (only 50 phones). We also need to remember that little is known about the specific characteristics of the various urban environments (number of passers-by, layout, time of day, etc).
For those who are too impatient to read the full study, here is a summary of the results:
Source Symantec Smartphone Honey Stick Project
People who found the smartphones:
- unlocked the device in 96% of cases
- accessed personal data and applications in 89% of cases
- accessed business data and applications in 83% of cases
- accessed both personal and professional data and applications in 70% of cases
- contacted the owner in 50% of cases
Viewing sensitive data was the primary goal of many people who found phones:
- they attempted to open the professional email inbox in 45% of cases
- they opened data marked “human resources” under “salaries” in 53% of cases and under “files” 40% of cases
- they opened “remote administration” application in 49% of cases
Curiosity was obviously a motivating factor:
- data or at least one application was opened in 96% of cases
- personal photos were opened in 72% of cases
- banking applications were opened in 43% of cases
- personal accounts (social media, messaging) were opened in 60% of cases
- the “passwords” file was opened in 57% of cases
Since 50% of smartphones were returned to their users, the results can be interpreted positively (as Symantec researchers did) or negatively.
recommendations
What can we learn from this study? Not much, except how important it is to take measures to protect your personal and professional information (e.g., passwords).
Vincent
credit photo : © vege - Fotolia.com

I work for Orange Business as a security leader within Products and Services Development. My previous jobs as a technical "worker bee" lead me to pay specific attention to the difficulties of implementing companies' security strategies and policies. Security, efficiency and pragmatism are my main pillars.