In early May 2011, the Czech Republic hosted the "Security and Protection of Information" conference, featuring an opening speech on "Denial-of-service (DoS) attacks using white horse systems: new proof-of-concept DoS against the domain name system (DNS) servers".
The presentation covered a new attack method that denies service on DNS servers using spam campaigns.
the idea
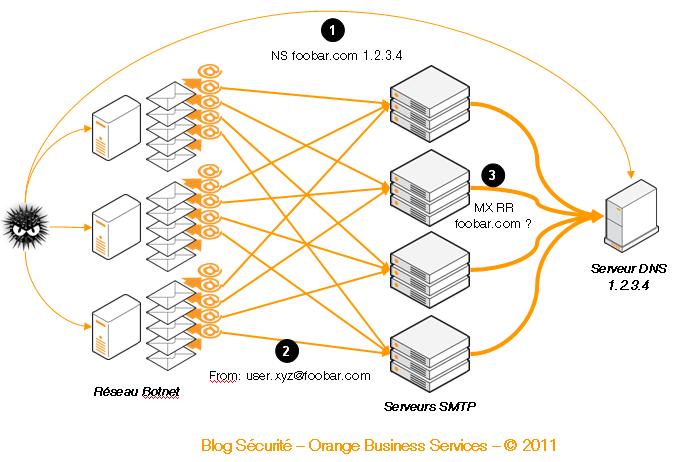
Below is the theoretical architecture presented by researchers Jakub Alimov (seznam.cz) and Minor (zone-h.org) in their article.
appetizer: DNS toast
This tasty bite is standard because attackers modify the DNS zone with a domain name in order to register the target server as a name server (e.g., foobar.com NS 1.2.3.4). Any Simple Mail Transfer Protocol (SMTP) server attempting to send an email to the domain name has to collect all necessary information (as outlined by Request for Comments 2821 by asking the responsible DNS server (in this case, 1.2.3.4).
first course: spam salad
The first course of attacks features typical techniques that send spam using the address(es) belonging to a domain previously declared on the DNS server (e.g., user.123@foobar.com, user.456@foobar.com). It is also possible to use sub-domain names (e.g., user.789@dummy.foobar.com).
Note: researchers have identified more than 14,000 unique IP addresses (apparently issued by the same botnet) for spam operations.
main course: white horse steak
The chef’s secret here is using what researchers call “white horses,” which are servers with high bandwidths. Big SMTP server hosts such as Yahoo Mail, Microsoft and Google are favorite targets.
Since each one has the strength to hit hard, these servers can effectively fight spam attacks, although many cases require an analysis of the sender’s legitimacy. In compliance with the RFC in force, SMTP servers verify all information associated with the domain name of each message (in this case, a "MX RR" or "A RR" DNS request for the foobar.com zone).
Researchers note that it’s possible to use a botnet of 50,000 machines, with each machine sending messages to 100 different white horse systems.
dessert: DNS medley with distributed DoS sauce
To perform their task, SMTP servers directly or indirectly ask the responsible DNS server about the domain name, directing a large volume of DNS requests to the target server (in this case, 1.2.3.4).
As the server does not necessarily have the capacity to handle these requests, it becomes a victim of service denial. As a reminder, servers requesting information are among the white horses that have access to significant resources.
Working with the figures listed above, we quickly arrive at 50,000 machines x 100 white horses x 1 message = 5 million messages or MX RR requests to the targeted DNS server.
anti-indigestion remedies
Protecting DNS zones is obviously the first line of defense. However, nothing can guarantee that a cyber-squatted zone will not choose your DNS server as a target.
Blacklisting the domains in question is also an easy form of protection, but it is not very effective. Attackers are free to use several domain names during operations (thus adapting their spam campaigns to blacklists).
Only protection mechanisms on the white horse side will be effective, such as anti-spam protection and setting up rules to limit DNS request streams.
Another solution is anti-distributed DoS protection, which can be set up with or before your infrastructure.

I work for Orange Business as a security leader within Products and Services Development. My previous jobs as a technical "worker bee" lead me to pay specific attention to the difficulties of implementing companies' security strategies and policies. Security, efficiency and pragmatism are my main pillars.