In late 2020, cybercriminals used U.S. IT infrastructure management software company SolarWinds as a springboard to launch an unprecedented attack on U.S. government agencies and high-profile enterprises, including Microsoft. The breach is rumored to have involved more than 1,000 professional hackers and officially compromised over 100 SolarWinds customers who use its Orion proprietary software to manage IT resources.
A backdoor into global networks
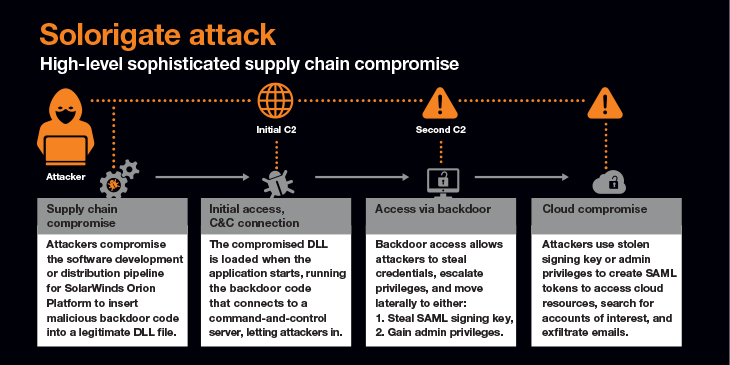
In short, hackers managed to add malicious code to SolarWinds' Orion network performance monitoring product. The action triggered a chain of events, resulting in SolarWinds unknowingly sending out software updates to customers that included hidden malicious code. Once inside the customers' systems, the software created a backdoor that the hackers used to inject Sunburst malware, enabling them to move around, control computers and spy on the organizations. "It is the largest and most sophisticated attack the world has ever seen," Microsoft President Brad Smith said at the time.
There has been no confirmation on who launched the attack, but many believe it may have been state sponsored.
Managing risk effectively
What makes the SolarWinds hack so important is its simultaneous depth and breadth. The sophisticated Sunburst malware gave the hackers access to entire government and enterprise networks worldwide, in turn accessing their and customers' sensitive data.
Today's supply chains are highly complex and interdependent, which exposes them to a growing threat landscape. The number one takeaway is that compromises and breaches are almost inevitable. Even when following best practices, the most prominent enterprises globally, including significant security vendors, could not prevent the compromise from happening.
The use of trojanized software updates across the supply chain to launch the SolarWinds attack is exceptionally worrying to enterprises. Why? Because enterprises can't see what they can do differently to stop this from happening again.
As a start, enterprises must immediately review their supply chains. They then need to create a proactive risk management strategy that aligns with their supply chains’ makeup.
Dealing with a dynamic threat landscape
Enterprises must also recognize that the threat landscape isn't static. It is dynamic, fluid, and requires an intelligence-based approach, points out Charl van der Walt, Head of Security Research at Orange Cyberdefense.
In the future, van der Walt says that the SolarWinds attack has highlighted how interdependent we all are in this fast-accelerating digital world. As a result, he hopes it will "encourage the development of a more holistic form of risk assessment that considers not only the risk posed to us by third parties but also the risk our failures may pose to our suppliers, customers and society as a whole."
"We can't think of the impact of an attack on an individual business. Every time there is a security failure, it has implications on the digital web that the business environment has created. This is why SolarWinds happened and will happen again unless enterprises take action," he explains.
Supply-chain incidents, in general, illustrate how related businesses are including using the same software from the same vendors. "Risk can't be calculated from a single company's perspective," explains van der Walt. "There needs to be a recalibration of how we understand vulnerability, impact and risk in general to reflect this 'interdependent' reality."
The big issue is that if SolarWinds’ flagship product can compromise government agencies and multinationals, many other vulnerabilities could be currently being exploited across all hardware and software in the supply chain, including major databases and operating systems.
Enterprises must have a clear view of their systems, software, infrastructure and supply chain to fully understand any possible attack surfaces. This is the all-important starting point for intelligence to predict future activities on the infrastructure.
Organizations should also take this opportunity to test "what if" scenarios by assuming they were impacted, advises Gartner. This encompasses mitigations or security defenses that would have provided effective containment and what would not. "This type of analysis may change thinking about security priorities and procedures," says Peter Firstbrook, Gartner Analyst.
"We need to be able to understand our environments, perceive changes in the threat landscape that might impact us, and respond quickly to patch, remediate or otherwise address the risk," advises van der Walt.
There is no security silver bullet
There is no simple security model, no checklist, no framework and no shopping list of technologies that cover all your risks. Bad actors are continually raising the bar, developing even more sophisticated tools and techniques. Enterprises need to be agile and innovative in their response, using intelligence-led security to stay one step ahead of attackers.
The SolarWinds incident will dominate the cybersecurity landscape for some time to come. Download the Orange Cyberdefense Winds of Change whitepaper to learn more about the attack's underlying causes and implications.