Over the last month or so I noticed a re-occuring notion in my Twitter feed. It came at me from @wired , @orangebusiness , @WSJ and various retweets by friends and Twitter connections. At first it seemed like just another bubbling up of security concerns.
when the NY Times and Wired disagree over... passwords!
On Nov 7th the New York Times published an article on securing yourself online "How to Devise passwords to drive hackers away" and I saw a few tweets about it. Honestly, I pulled up the link but didn't really give it more than a glance as I assumed it was another article about using a number in your password and making it a phrase. Both are decent suggestions but I had seen this "news" before.
As the week wore on I noticed several tweets and re-tweets about a Wired magazine story "The New York Times Is Wrong: Strong Passwords Can’t Save Us". This got my attention since it was one major publication calling out another. There were follow-up links to the main Wired cover story, "Kill the Password: Why a String of Characters Can’t Protect Us Anymore". That is when I started to read instead of skim (I suggest you do the same) and that's when I got hooked.
what Orange Business bloggers have to say about that
After digesting the Wired story and the original NY Times article I went to our Orange blog to see what we had in our security tags. Coincidentally one of our bloggers had a very good post with this interesting graphic (passwords: the key to keeping your secrets locked up tight ).
Basically it tells you how long it would take to process a hack on your account based on how long and complicated your password happens to be; the main quote "If your password has over 13 characters, you can assume it will be nearly uncrackable".
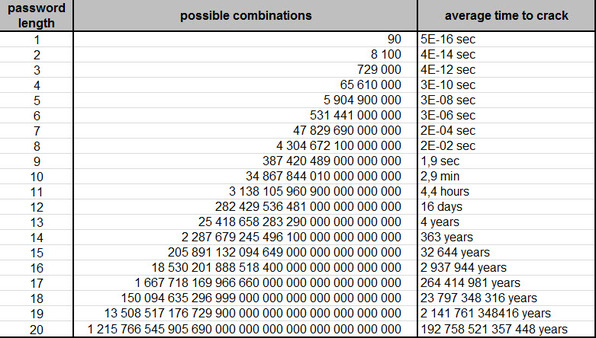
so what should we learn from that?
Until I had read the Wired article, I would have agreed with the NYT and our blogger almost entirely. A long complicated password should be enough. In fact, I have said a version of this next statement to many friends and relatives; "just make sure your password isn't in the dictionary. Hackers aren't going to waste time to get at your AOL email."
But the vulnerability in reseting those passwords or the shear collosal task in managing a 12+ character password for each account made me realize that I needed a plan. So I went back to the Wired author's main regret, if he had turned on two-factor authentication for his Gmail, the hack would have ended there.
conclusion and next step
And that is what I did. Not just for me but for every family member that was lucky enough (or unlucky, since they had to deal with me) to have brought their laptop to our Family Thanksgiving weekend. It took about 8 minutes per person to turn on the feature, secure their laptop, iPad, phone and associated apps that rely on a Gmail login.
Now be aware, that was 8 minutes per person but I did not click on all the buttons or enter the passwords. I simply walked each person through the process so they could se what exactly was being enabled and how it would affect them. Which is to say, not at all.
Part two of this adventure will walk you through how easy it is to turn on two factor authentication for Google and Dropbox plus a bit about the market. If you have worked in IT for more than a few years, you have likley carried one of those RSA keyfobs. They just might be a thing of the past.
Joshua
picture credit: © asrawolf - Fotolia.com

Joshua Sillers has been with Orange for the past 12 years working to enhance the customer experience. He is currently serving as a Collaboration Sales Expert with an emphasis on Team collaboration tools, API interactions, Orange OpenLabs and User Adoption Services. Joshua holds a B.A. degree in International Relations and Spanish from Concordia College in Moorhead, MN and a Masters of Science in Technology Management from the University of Minnesota.