In the part one of this article, a Cleaning Center had been deployed against the attacks at the Orange subsidiary’s network connection points.
Posted behind their fortifications, the teams in charge of the service platforms waited for a possible new round of attacks. What strategy would the attacker use? Would the cleaning system withstand the new attacks?
It started all over again in July 2008.
late July 2008: the saga continues
The attack targeting the end customer surges again, first with two 40-minute volleys of server saturation targeted by a SYN flood. However, this ends very quickly.
Next, multiple sources begin a coordinated effort to open (too) many connections on one of the Orange subsidiary’s messaging servers. The Cleaning Center module then goes into “protection” mode.
Immediately, the illegitimate connections are filtered out. Realizing the failure of their efforts, the aggressors change their tactics and manage to open an apparently “legitimate” connection. As soon as they succeed, they use the connection to flood the server with requests.
The module then changes its protection mode by filtering out the malicious source address. Almost six hours later, the attack ceases. Though disruptive, the attack was not very strong. In fact, it never reached a rate of more than 1,000 packets per second.
early August 2008: a new, more elaborate attempt
The Cleaning Center detects a barrage of 80,000 packets per second targeting the original address of a customer that had received multiple attacks since July. Operations teams are alerted, but the attack quickly dies out. It was only a trial round.
Less than two hours later, the pirates renew their first attack with the same intensity. But this time it lasts. The customer’s website crashes once again due to the massive load received by the attack.
The team decides to activate filtering by shifting the module from “monitoring” to “protection” mode. The client server’s protection is now activated.
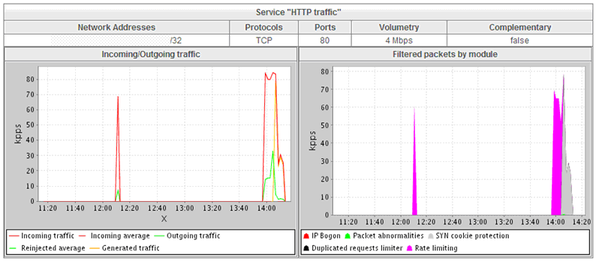
The Cleaning Center immediately begins to filter the attack. It detects and blocks the majority of spoofed addresses used by the pirate to launch a massive influx of simultaneous requests to open connections on the targeted web server.
Less than ten minutes after the start of the offensive, the attackers notice that their efforts are fruitless. They cease fire but reconfigure their botnet. The attack picks up again at a rate of 80,000 packets per second. It is automatically filtered.
Three minutes later, the pirates pad their original attack (SYN flood) with a massive influx of HTTP GET requests directed at the same web server. This attack (GET flood) comes from 97 machines (members of the botnet coordinated by the pirates), increasing fire to 175,000 packets per second.
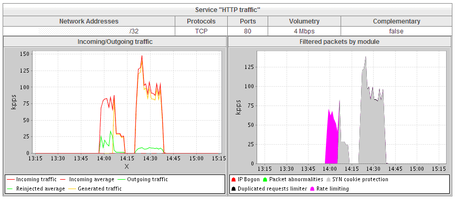
The “Cleaning Center” then adapts its protection to filter these new malicious requests.
the battle comes to an end
After nearly 40 minutes of fighting, the attack ends. The pirates no doubt recognize the failure of their attempt. The customer is now protected, and the attackers’ malicious intentions are neutralized by the Cleaning Center’s protection, positioned ahead of the target.
Taking advantage of the Cleaning Center’s onboard capture and storage features, the system updates the list of machines involved in the attack and manages to locate them. Unbeknownst to their legitimate owners, these machines had been wrapped into the botnet by the pirates.
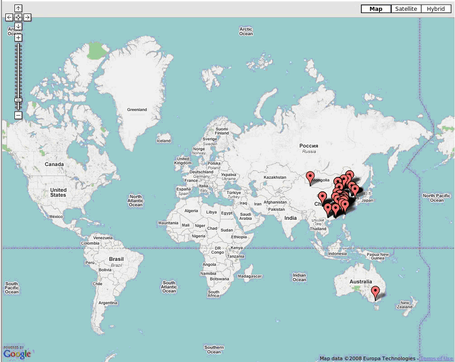
For the most part, the machines are located in China and Korea. After a more in-depth analysis conducted the following day, Orange Labs experts detect and extract one additional address of a machine acting strangely. It had repeatedly tested the website’s availability just before, during, and up to 4 minutes after the attack. Had we found our culprit?
conclusion
The success of this operation demonstrates the critical necessity to protect against distributed denial-of-service (DDoS) attacks by quickly mobilizing network experts and utilizing adapted, innovative, powerful tools. In this pseudo-arms race, the defense arsenal is varied. It’s imperative to know how to effectively use both the simplest and the most sophisticated techniques.
Again, hats off and my thanks to Emmanuel Besson and Pierre Ansel from Orange Labs for the high-quality content of this blog post!
Jean François
photo credit: © DURIS Guillaume - Fotolia.com
This blog post was originally published in French here.

Au sein de la direction sécurité du Groupe Orange, je suis en charge de la veille sécurité et de la sensibilisation à la sécurité. Franchise, optimisme et bonne-humeur sont mes moteurs quotidiens