Whether you are a project manager, IT manager, head of a development project, or in charge of any other activity involving direct user contact, you have undoubtedly heard the question: “Why are there so many password rules?”
The answer is strength. The stronger the password, the better it will resist attacks. As with a bike chain or padlock combination, the strength of the code often determines how much time an attacker will need to crack it.
The definition of strength depends on the type of threat. Here we will address brute-force attacks and cracking.
brute-force attacks
The goal of a brute-force attack is to discover a password by trying all possible combinations:
- in the case of an online application/system, the attacker aims to reach a screen other than the authentication page (which will indicate the operation’s success)
- in the case of encrypted data theft, the attacker tries to obtain “clear” content (decrypted file) or an identical encrypted password (attack by comparing results)
After all, who hasn’t attempted a brute-force attack on their old luggage lock after forgetting the combination?
strength criteria
There are three criteria for creating strong passwords:
- password length: the longer it is, the more possible combinations there are
- size of the character set: the longer the character set, the more available combinations
- password shelf life: the longer it’s used, the more vulnerable it becomes
We have set aside the issue of social engineering attacks, as they exploit weaknesses other than password strength.
tools
Many password generation tools are available in the form of user interfaces and libraries for developers.
However, the increasing number of passwords (for system sessions, inboxes, web interfaces, e-commerce sites, social networks, etc.) does not allow account managers to implement a policy that generates passwords for users.
The current (quite natural) trend is to enable users to define their own passwords while imposing a certain number of requirements to ensure password strength (using at least one capital letter, one special character, one number, etc.).
How should a password strength policy be created? Below are four online tools to help everyone approach this topic in a fun, educational way.
how secure Is my password?
The website howsecureismypassword.net attempts to answer the question in simple, layman’s terms. It shows users how long a machine (powerful enough to analyze 10 million combinations per second) would take to break a given password.
- informative value: low
- layman’s value: high
- target audience: uninformed users
- comments: giving a specific time period helps the tool raise awareness
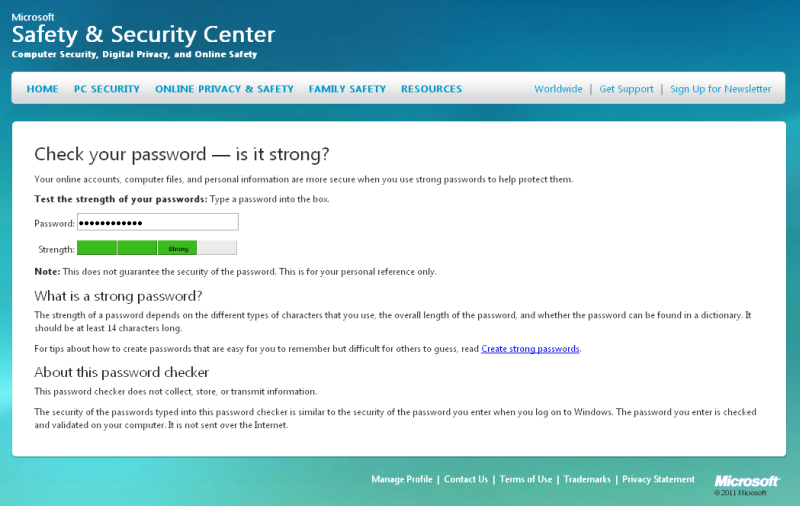
Microsoft Password Checker
The Password Checker tool in Microsoft’s PC security section is not on par with what the software giant could offer.
- informative value: low
- layman’s value: low
- target audience: uninformed users (those unfamiliar with security)
- comments: the primary colors make it look like a game for kids
Password Meter
Much more elaborate than the two previous tools, Password Meter explains the criteria it uses to assess password strength. It gives your password a grade of “Failure”, “Warning”, “Sufficient” or “Exceptional” in each of its categories.
- informative value: high
- layman’s value: average
- target audience: people who want to learn more about password strength criteria
- comments: though unattractive at first glance, the tool is highly informative
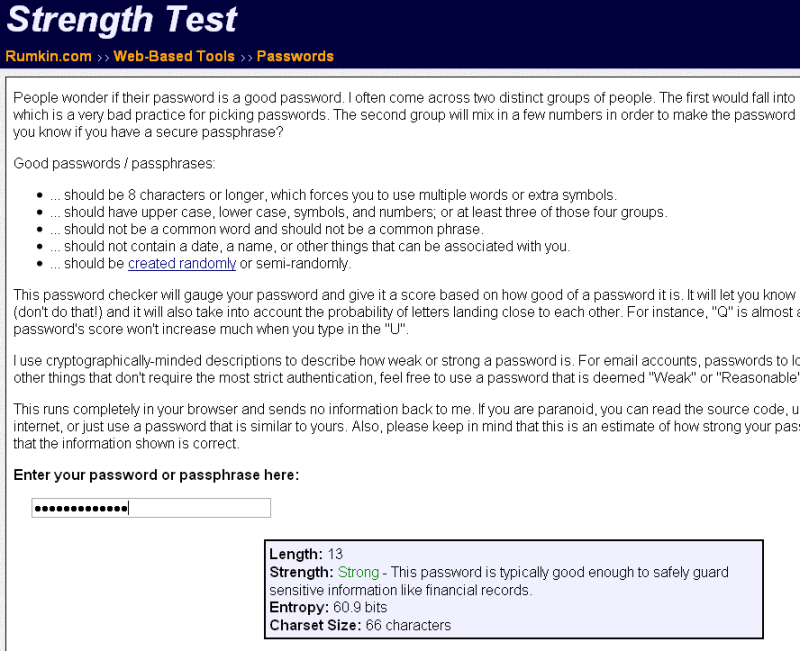
Password Strength Test
In the same vein, Password Strength Test has a pared-down look but provides a wealth of important information. It succinctly outlines the metrics used to generate the final grade (character set size, entropy). An accompanying text explains which contexts are appropriate for the password and how users can improve their score, if desired.
- informative value: average
- layman’s value: average
- target audience: people who want to learn more about password strength criteria
- comments: the tool’s visually austere display will not encourage use
additional notes
The technologies used by these kinds of websites rely on JavaScript. As a general rule, no data is transmitted to the server, which limits the risk of attackers hiding behind the tool’s host website. Nevertheless, using your real password is not recommended. It’s better to use a variation that moves or reverses certain characters, for example.
The websites listed above are in English, which may make it difficult for non-English speakers to understand the analyses they provide. If you know of any educational (non-commercial) password security websites in other languages, they will be added to this article with pleasure.
This article does not go into dictionary attacks. Indeed, many brute-force attacks begin with predefined combinations (first names, cities, common nouns, etc.), which can considerably speed things up. More complex mechanisms, like rainbow tables, also help significantly reduce the time needed to break a password.

I work for Orange Business as a security leader within Products and Services Development. My previous jobs as a technical "worker bee" lead me to pay specific attention to the difficulties of implementing companies' security strategies and policies. Security, efficiency and pragmatism are my main pillars.